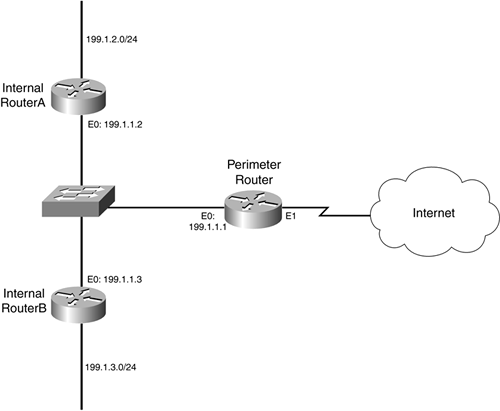
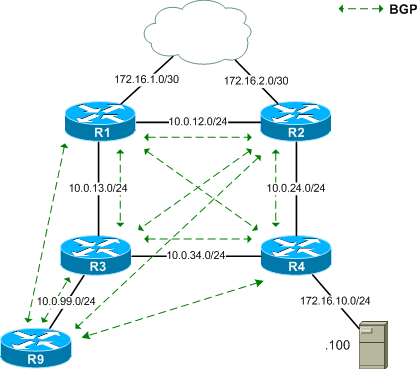
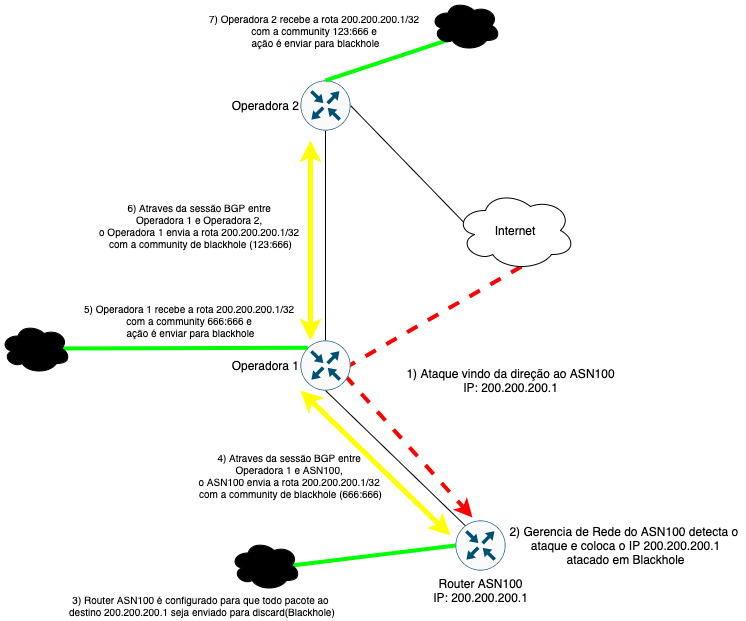
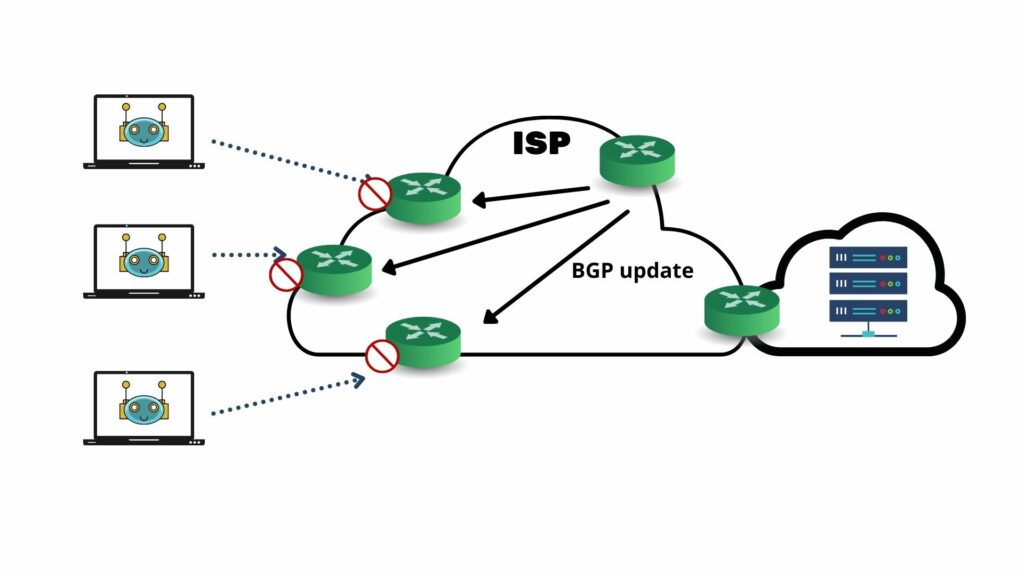
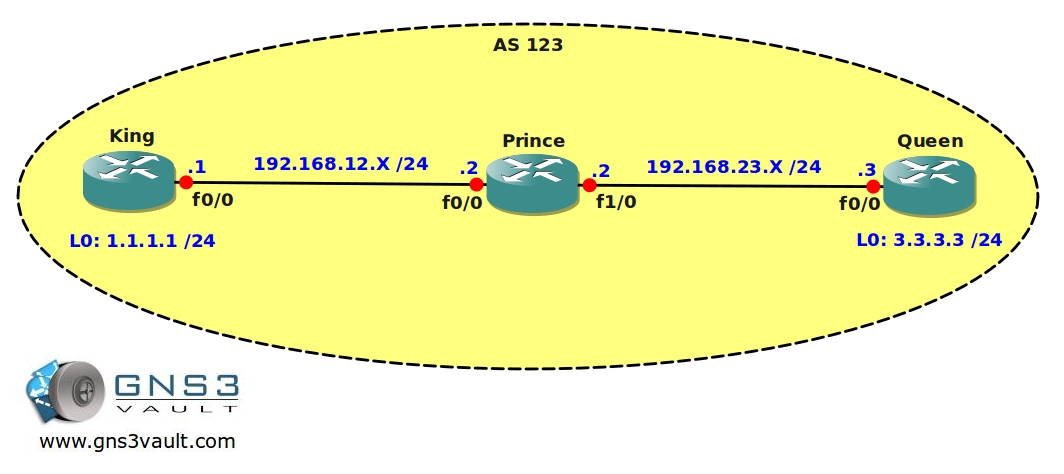
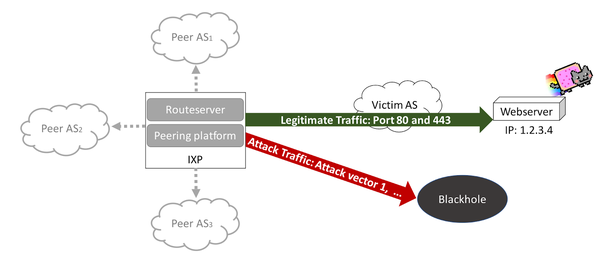
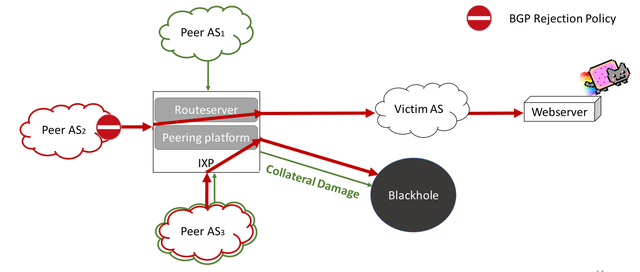
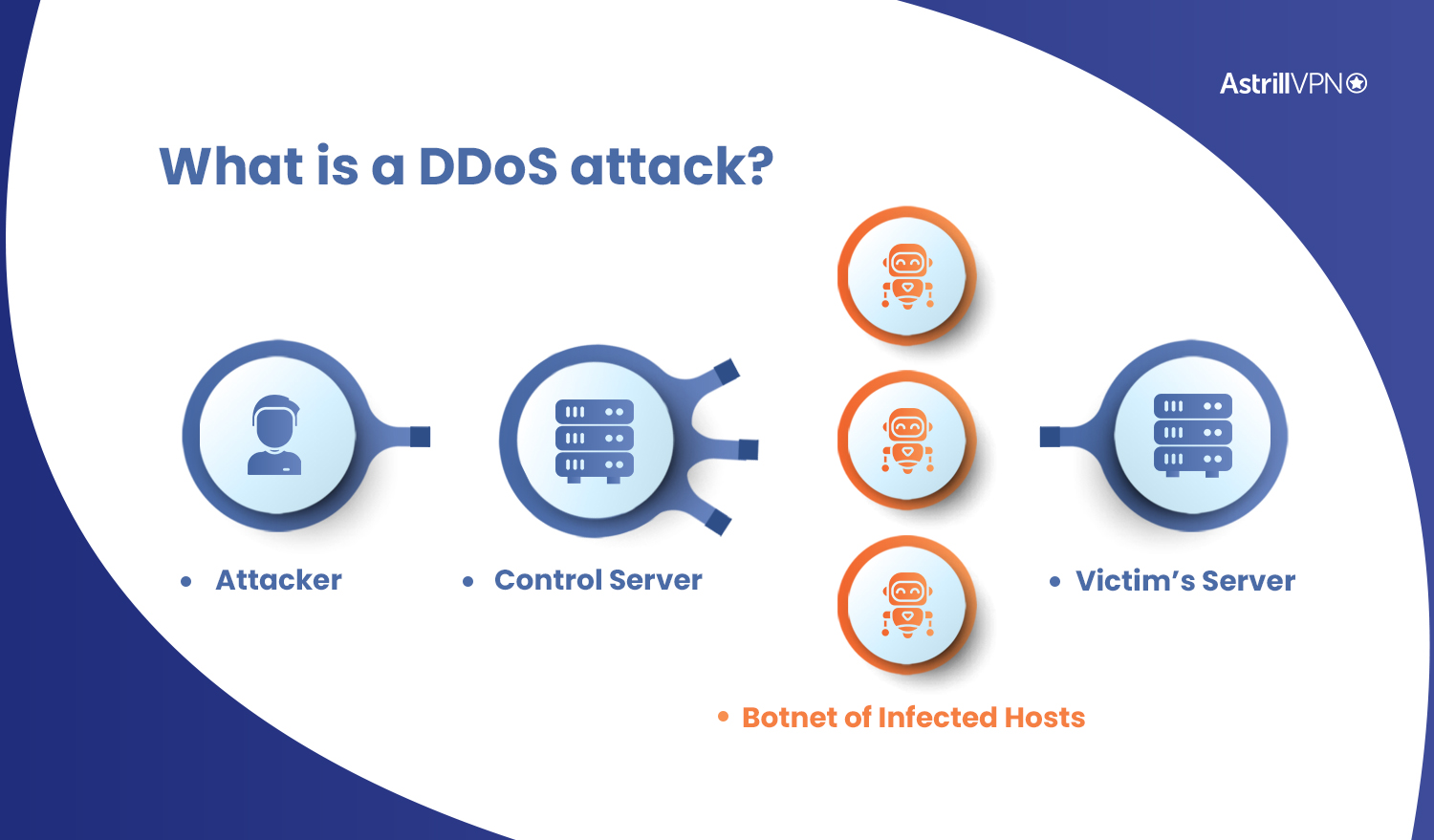
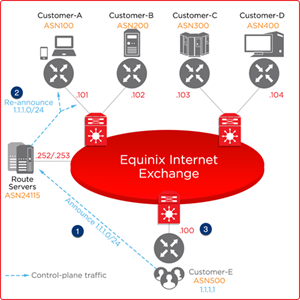
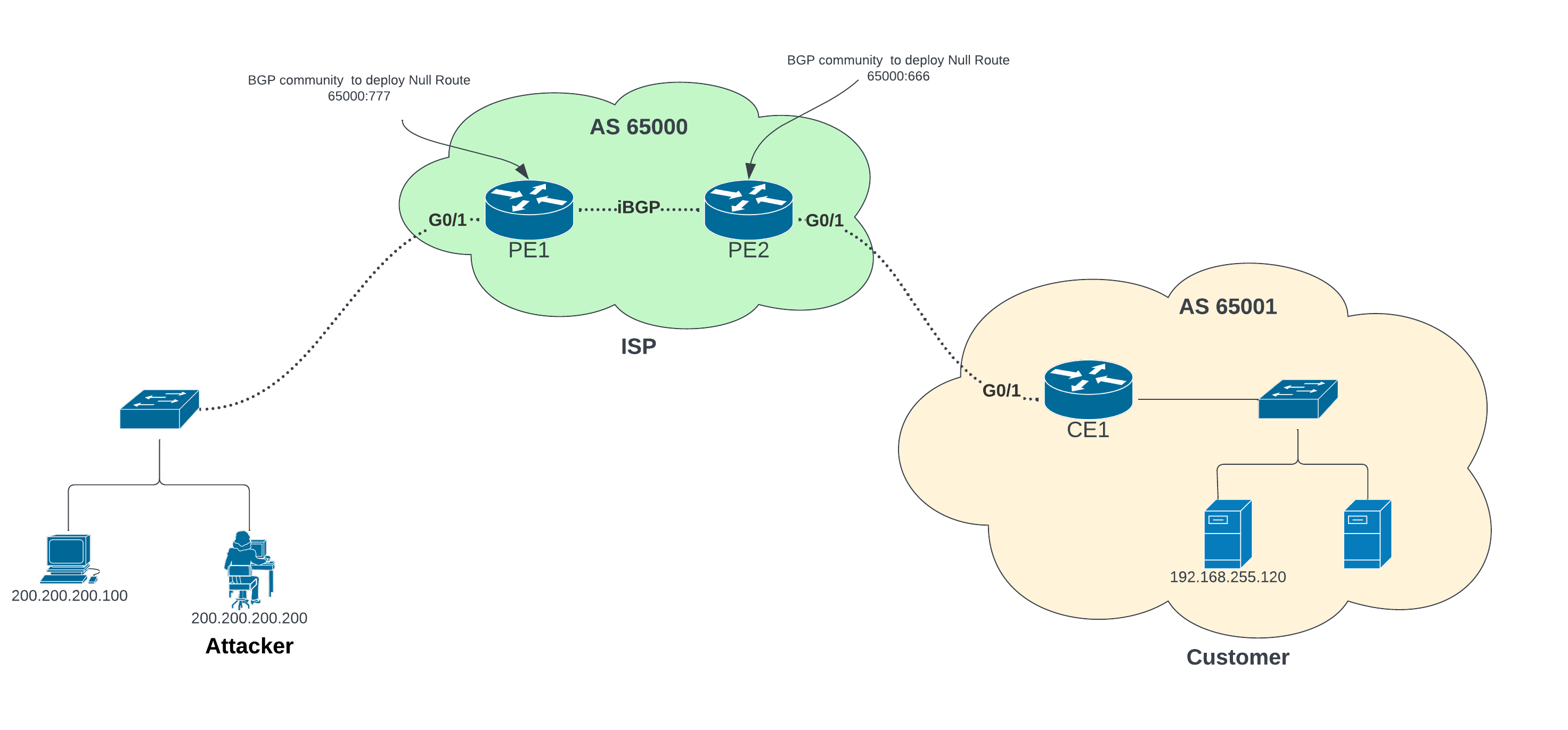
How to configure Remotely Triggered Black Hole routing to protect from DDOS attacks (with bonus) - RouterFreak
GitHub - auspost/aws-route-mon: Script that monitors AWS routes for black-hole routes, and corrects the situation if detected
![PDF] BP-AODV: Blackhole Protected AODV Routing Protocol for MANETs Based on Chaotic Map | Semantic Scholar PDF] BP-AODV: Blackhole Protected AODV Routing Protocol for MANETs Based on Chaotic Map | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4b2b3c0a1d274fadaaa6d9f3ce3a00d7509d5e3f/3-Figure1-1.png)
PDF] BP-AODV: Blackhole Protected AODV Routing Protocol for MANETs Based on Chaotic Map | Semantic Scholar